The healthcare industry in the U.S. is facing a worrying increase in data breaches, with a staggering 8.8 million health records compromised in just January 2024. This complicated trend highlights the critical need for strict adherence to HIPAA regulations. Failure to integrate can result in hefty fines of up to $68,928 per violation, with an annual cap of $2,067,813.
As if the financial penalties weren’t enough, 2024 is expected to bring even more rigorous enforcement of HIPAA regulations by the Office for Civil Rights (OCR).
Given these circumstances, it’s now essential for healthcare providers to develop HIPAA-compliant mobile apps. This guide provides a step-by-step method to ensure your app meets HIPAA’s stringent standards, protecting sensitive patient data.
What is HIPAA?
HIPAA means the Health Insurance Portability and Accountability Act, enacted by the U.S. Congress in 1996 to safeguard sensitive medical information. It ensures patient privacy and data security while promoting the healthcare system’s integrity.
HIPAA applies to healthcare providers, health plans, and clearinghouses, requiring strict protocols to protect patient privacy. However, before implementing HIPAA compliance in your mobile app, it’s essential to understand the types of data it handles:
Protected Health Information
Protected Health Information (PHI) is any data identifying an individual’s health status or care. This includes medical records, billing details, and healthcare-related conversations. For example, if a mobile app stores a patient’s medical history, lab results, or treatment plans, it must comply with HIPAA to secure this PHI.
Confidential Health Information
Confidential Health Information (CHI) includes health-related data from non-traditional sources like wellness apps or fitness trackers. This can involve data on exercise routines, dietary habits, or heart rate measurements.
Once you understand the type of data involved, it becomes clear how crucial HIPAA is in protecting sensitive health information. Compliance with HIPAA regulations not only safeguards the privacy and security of individuals but also strengthens trust between patients and healthcare providers.
What Healthcare Apps Must Comply with HIPAA Regulations?
Any healthcare app that handles PHI must comply with HIPAA regulations, such as those for telemedicine, Electronic Health Records (EHR), patient portals, or medical devices.
Entity
Entities refer to organizations or individuals involved in healthcare transactions that access PHI. Their classification under HIPAA determines their obligations. Two types of entities must comply with HIPAA regulations.
Data
The type of data healthcare apps manage is critical in determining HIPAA compliance. PHI, which includes individually identifiable health information, is subject to strict security & privacy rules under HIPAA.
Security
Security is a core factor in determining whether healthcare apps should follow HIPAA, especially when protecting electronic protected health information (ePHI). ePHI refers to any protected health data transmitted, stored, or maintained electronically.
Overwhelmed by Mobile App Compliance?
Discover how to build HIPAA-compliant apps with our step-by-step guide.
Steps to Develop HIPAA-Compliant Mobile Apps
As an AWS Healthcare Competency Partner, we possess the necessary expertise to ensure that your mobile app fully complies with the stringent security and HIPAA regulations.
Types of Safeguards
Here’s how HIPAA rules impact your mobile app development:
Technical safeguards
Encrypt patient information at rest and in transit using strong encryption protocols like AES-256 to safeguard it from unauthorized access or interception.
Implement robust authentication mechanisms such as biometric or multi-factor authentication to verify user identities accessing the app.
Use secure coding practices like input validation and parameterized queries to protect against vulnerabilities, such as SQL injection or cross-site scripting, which could expose ePHI.
Regularly update your app and its underlying software to patch known vulnerabilities and protect against emerging threats.
Set up monitoring and logging systems to track data access, detect unauthorized activities, and quickly respond to suspicious behavior.
Physical safeguards
Restrict physical access to devices or servers containing patient data by applying strict access controls and securing them in designated safe locations.
Ensure encryption and password protection for mobile devices accessing patient information to prevent unauthorized access in case of theft or loss.
Adopt secure disposal policies for old devices, ensuring data is wiped completely before disposal.
Train employees on the importance of physical security and enforce strict protocols for handling mobile devices that store patient data.
Regularly review and update physical security measures to address environmental risks or changes.
Administrative safeguards
Create and enforce policies that govern the secure handling, storage, and transmission of patient data, including guidelines on employee use of mobile devices.
Provide regular HIPAA training to employees on best practices and maintaining patient privacy.
Appoint a HIPAA compliance officer to oversee security measures and conduct regular risk assessments.
As HIPAA requires, protocols for handling security incidents, including notifications to affected individuals and authorities, must be established.
Conduct regular audits and risk assessments to improve HIPAA compliance and adhere to regulatory standards continuously.
The Process of Building HIPAA-Compliant Mobile Apps
Developing a HIPAA-compliant app requires a well-rounded strategy to safeguard sensitive patient information:
Step 1: Choose and integrate a HIPAA-compliant backend service
Choose a HIPAA-compliant backend provider, like AWS, Microsoft Azure, or Google Cloud, along with their compliant services and data centers. For example, AWS offers HIPAA-eligible services such as EC2 for computing, S3 for storage, and RDS for databases. Google Cloud’s Cloud Healthcare API also offers a HIPAA-compliant platform for storing and analyzing PHI.
Step 2: Isolate PHI from general app data
Design your app architecture to separate sensitive data (PHI) from non-sensitive data using distinct databases or stores. This separation reduces the risk of unauthorized access to PHI. For example, in iOS development using Swift, separate data models for PHI are created. Android (Java/Kotlin) uses separate databases or content providers.
Step 3: Secure sensitive data through encryption
Apply strong encryption algorithms like AES-256 and protocols like TLS/SSL to secure data at rest (in databases or files) and in transit (during network transmission) throughout its lifecycle.
Step 4: Perform comprehensive security testing on the app
Regularly test your app for security vulnerabilities through penetration testing, vulnerability scanning, and code reviews. Partner with reputable third-party security firms or use automated testing tools like Nessus, Qualys, or OWASP ZAP to ensure thorough evaluations. This also includes auditing encryption methods, access controls, and transmission protocols.
Step 5: Enable application logging and monitoring systems
Establish detailed logging systems to record user activities, system events, and access to sensitive data. Use real-time monitoring tools like Prometheus, New Relic, or Datadog to detect suspicious activity in your app’s infrastructure.
Step 6: Implement strong identity and access management
Establish strong identity and access management (IAM) policies to ensure only authorized individuals can access PHI. To maintain tight control, implement role-based access controls, multi-factor authentication, and regular access reviews. Tools like Auth0 or Okta can help you establish compliant IAM protocols.
Step 7: Enforce data integrity
Measures must be put in place to maintain the integrity of PHI, using data validation techniques and digital signatures to prevent unauthorized modifications. Keep an immutable audit trail to track any changes to PHI, including details about who made the changes and when.
Step 8: Ensure secure disposal of sensitive data
Securely dispose of PHI when it’s no longer required, following HIPAA guidelines. Implement data retention policies that define how long PHI should be kept and ensure secure destruction methods like cryptographic erasure or physical destruction of storage media.
Step 9: Finalize a HIPAA-compliant business associate agreement (BAA)
Sign a HIPAA-compliant Business Associate Agreement (BAA) when working with third-party vendors. The BAA should include terms for data security, breach notification, and adherence to HIPAA standards.
Best Practices to get HIPAA Compliance for Healthcare Apps
Building a HIPAA-compliant app is a significant investment. Follow these tips to ensure your app complies with HIPAA and protects sensitive health information, avoiding costly fines.
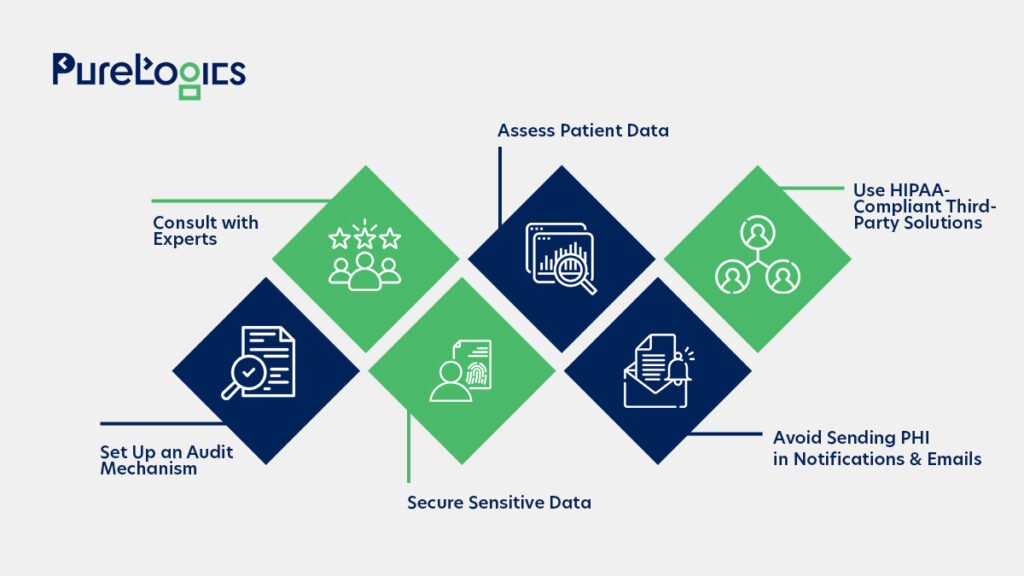
Consult with Experts
HIPAA regulations are complex and change over time. Work with legal professionals specializing in healthcare privacy laws to ensure you’re up-to-date on the latest requirements. HIPAA-certified compliance officers can help implement administrative, physical, and technical safeguards.
Consider collaborating with healthcare IT consultants or cybersecurity firms experienced in HIPAA compliance. They can provide risk assessments, develop tailored compliance strategies, and offer ongoing support and training for your team.
Assess Patient Data
Perform a detailed data mapping exercise to identify all the patient data your app collects, processes, or stores. Determine which data qualifies as PHI and falls under HIPAA regulations. Implement systems to classify and protect PHI, such as access controls and encryption.
Use HIPAA-Compliant Third-Party Solutions
If your app relies on third-party services like cloud storage, data analytics, or payment processing, ensure these vendors are HIPAA-compliant. Carefully evaluate their security practices, data handling procedures, and certifications.
Review their encryption protocols, access controls, and breach notification policies. Be sure to sign Business Associate Agreements (BAAs) with these vendors, clearly defining their role in protecting PHI.
Secure Sensitive Data
Implement strong security measures to protect PHI throughout its lifecycle. Encrypt data at rest (stored on servers or devices) and in transit (during transmission) using encryption standards like AES-256 or higher.
Apply strict access controls, including multi-factor authentication, role-based permissions, and regular password updates, to limit who can access PHI. Use secure communication protocols like HTTPS and TLS to transmit PHI online.
Set Up an Audit Mechanism
Establish a system to track and log all activities related to PHI within your app. This should include recording when PHI is accessed, modified, or transmitted and identifying the users involved.
Deploy centralized logging and monitoring solutions that collect and analyze audit logs from applications, databases, and network devices. Regular audits help identify potential breaches and allow for prompt investigations and responses.
Avoid Sending PHI in Notifications and Emails
Refrain from including PHI in notifications, emails, or other communications unless necessary. If essential, ensure the communication is encrypted and meets HIPAA standards.
Use secure messaging platforms with end-to-end encryption to facilitate PHI sharing. Train your users on handling PHI properly in communications and highlight the risks of using unsecured channels.
Concerned about the costly consequences of HIPAA violations?
We specialize in crafting secure, HIPAA-compliant mobile applications tailored to your needs.
PureLogics Ensures HIPAA Compliance in Mobile App Development
Building HIPAA-compliant apps requires more than just typical mobile app development skills. It necessitates an in-depth understanding of HIPAA regulations and a systematic approach to ensuring compliance throughout development.
As an experienced technology partner, PureLogics has a proven history of delivering HIPAA-compliant healthcare applications to numerous clients. Our comprehensive approach to HIPAA compliance includes the following:
- Detailed risk assessments
- Advanced data encryption techniques
- Secure user authentication and authorization processes
- Rigorous access control measures
- Strict audit trails and logging systems
- Regular security updates and patches
- Extensive employee training on HIPAA compliance protocols
- Continuous support and maintenance to ensure ongoing compliance
Additionally, as an AWS Partner, we excel in streamlining workflows, automating processes, and keeping patient care at the forefront.
Partner with PureLogics today to begin your journey toward developing a secure and compliant HIPAA-approved mobile app.


 [tta_listen_btn]
[tta_listen_btn]
 October 2 2024
October 2 2024