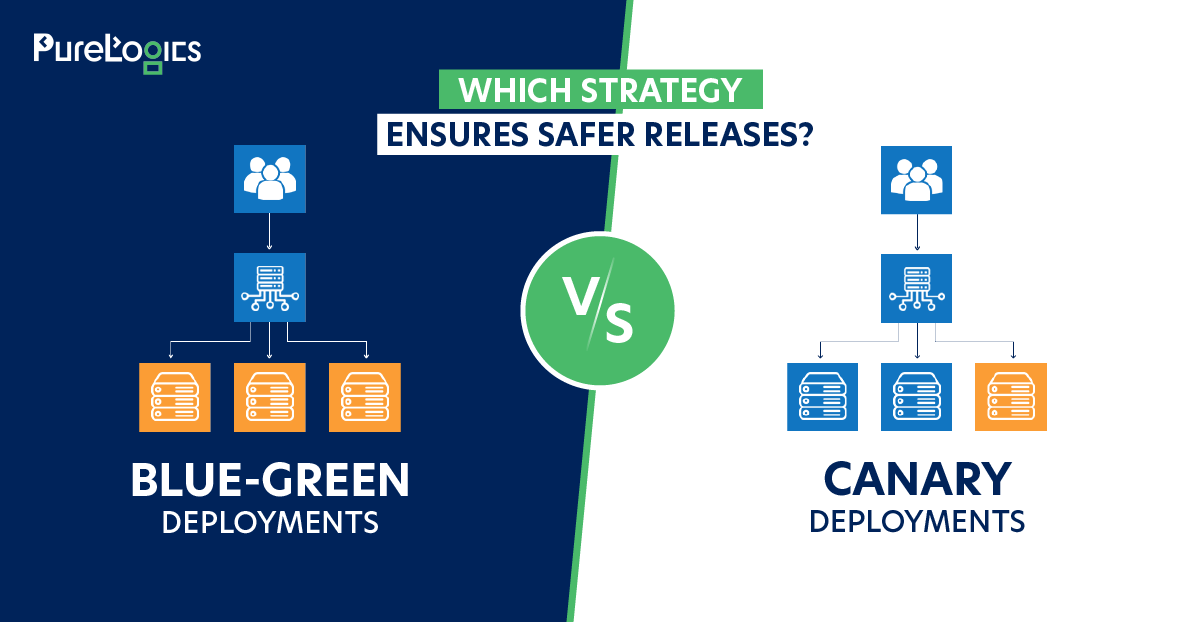
Security engineering moves at lightning speed, which makes staying current a necessity. Falling behind isn’t an option.
Our experts field questions from software developers worldwide, shedding light on major compliance frameworks, top cloud and AWS security checks, and the vital role of DevSecOps in cloud environments.
Worried about cloud security vulnerabilities?
Enhance your cloud security strategy— explore our services!
Getting Started with DevSecOps and Cloud Security
What are the responsibilities of a security engineer?
A security engineer protects an organization’s digital assets and data from cyber threats. They identify risks, design and implement security measures, and enforce policies and procedures to ensure the integrity and confidentiality of IT resources. Security engineers conduct regular audits, manage vulnerabilities, and respond to security incidents, striving to prevent breaches and minimize their impact.
Could you share some insights on how to pursue a career as a security engineer?
To become a security engineer, you should pursue higher education in computer science, information technology, or cybersecurity. Internships in these fields can be valuable for gaining practical experience. Developing a strong foundation in programming languages, operating systems, and networking concepts is essential.
Additionally, familiarize yourself with cybersecurity and DevOps fundamentals, such as encryption, access control, and security protocols. Alongside technical skills, effective communication and problem-solving abilities are crucial for success in this field.
What exactly is DevSecOps, and how can organizations new to it seamlessly integrate security into their DevOps practices? For beginners, what is the best approach to establishing a security-centric culture?
DevSecOps is the most critical transformation a business can invest in this age. Automation is a caretaker, erasing errors and operating independently of human flaws. Manual operations and repetitive tasks often lead to mistakes and carelessness, making us inefficient and causing us to lose focus and interest. As humans, we thrive on challenges and new experiences. Who wants to deploy identical machines endlessly, run the same rules, or read source code forever? We doubt anyone does.
DevSecOps integrates three main IT components: development, security, and operations. Merging these vast areas is challenging, and managing them as a unified entity is even more difficult. From my experience with various CI/CD pipelines, I’ve seen how eliminating manual operations instantly boosts efficiency.
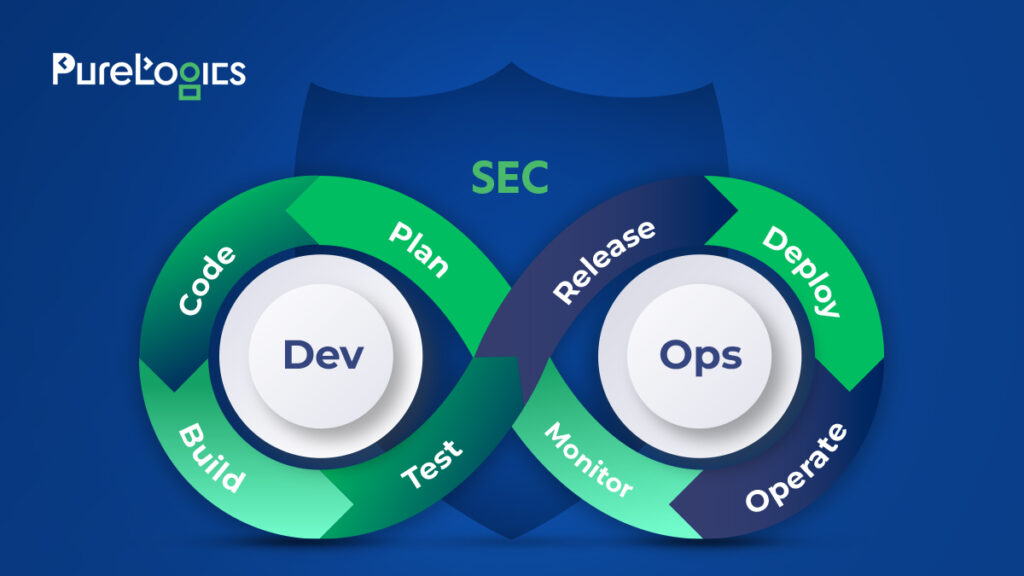
Cultivating a security culture is tough—almost impossible to foster internally. Set-in-their-ways employees will resist, and you’ll need guidance to navigate this transformation. Often, this means bringing in a consultancy to lead the way.
Best Practices and Security Considerations for Enterprises
What are the key distinctions between main compliance frameworks? Are any of these frameworks particularly well-suited to specific industries?
Frameworks and standards are the same when applied to entities or assets, but they vary across industries. For instance, a firewall functions similarly, regardless of location. When you assess entities by their attributes, they will behave consistently within any framework.
However, the purpose of these entities or assets changes depending on the industry. For example, a web server might manage financial data for a banking company but handle personally identifiable information (PII) for a healthcare institution: same entity, different sector, different outcomes.
ISO 27001 is the most common security standard. Many other standards and frameworks are based on ISO 27001, making it a great starting point for any industry. Applying ISO 27001 to your daily work helps you understand it more effectively.
What fundamental security checks would you recommend for testing a web application?
The top 10 list from the Open Web Application Security Project (OWASP) is essential for web application security, and we highly recommend it to everyone. This list comprises standardized, developer-friendly resources to help organizations identify, prioritize, and mitigate the most critical security vulnerabilities of web applications. The best part? It’s regularly updated to reflect the latest threats and best practices.
With the wide range of AWS offerings, where should teams begin regarding AWS security best practices? Which services are the most critical to secure?
The answer to this question largely depends on the specific services you’re using. AWS is an extensive ecosystem with many tools and services at every level of the tech stack. Some fundamental areas to start with include:
- Identity and Access Management (IAM)
- Web Application Firewall (WAF)
- Virtual Private Cloud (VPC)
- CloudTrail
- S3 Bucket Security
- Infrastructure as Code (IaC) tools
These tools are essential for most AWS users operating at scale. Depending on your particular use case, other data security and automation tools might be beneficial. Consulting with an AWS specialist can help you determine your needs and identify the best tools for your environment.
Cybersecurity: What’s the Future?
Can you explain how advancements in generative AI have influenced our work?
Engineers pave the way, and generative AI follows. Experts instruct it to create unique documentation sets to comply with specific frameworks for companies. Developers rely on it to check code for vulnerabilities or to assess whether a configuration file might lead to a cybersecurity attack.
Generative AI represents a new frontier in the field. We use it daily, and we find it especially useful for quickly learning how to use new tools and technologies.
What challenges arise when implementing Zero Trust Architecture (ZTA) in cloud-based environments?
Zero Trust Architecture (ZTA) embodies the principle of “never trust, always verify,” countering the traditional “implicit trust” approach, in which users and devices are trusted once verified and connected to a network. ZTA focuses on privilege management, aiming to prevent malicious actors from moving laterally through the network to access sensitive information they are not authorized to reach.
However, ZTA is often misunderstood because security vendors rebrand their products to leverage the term’s novelty, even when it may not be relevant. They frequently market firewalls, endpoint protection platforms, or access management tools (like IAM) as embodying ZTA, which needs to be more accurate. Applying a security product to a network differs from maintaining a security culture within that network; every product can only replace the ongoing effort required to implement ZTA effectively.
Before implementing ZTA, it is crucial to consider the roles of all stakeholders, shareholders, suppliers, and connections. The cloud aims to provide a more flexible and open environment than traditional enterprise software. To achieve this, companies must meticulously identify what needs to be protected. Safeguarding confidential information is an ethical duty and beneficial for business. Securing your economic assets builds trust and maintains a competitive edge.
Concluding Thoughts
In conclusion, DevSecOps and cloud security are critical components in today’s rapidly evolving digital marketplace. As organizations increasingly adopt cloud technologies, integrating security at every stage of the development lifecycle is no longer optional—it’s essential. Our expert insights underline the importance of a proactive and robust approach to safeguarding data and systems.
At PureLogics, we offer cutting-edge cloud services with high-end security measures that help businesses stay ahead of threats and ensure their operations remain secure and resilient. Trust PureLogics to be your partner in building a secure digital future. Give us a call today!


 [tta_listen_btn]
[tta_listen_btn]
 August 30 2024
August 30 2024